Overview
ThreatLIST provides SIEM enrichment options for network, security, and incident response professionals.
Our database of IP addresses and domain IOCs can be used to enhance research and forensics, local reporting and network traffic correlation, and as a data enrichment tool for SIEM software (Splunk, QRadar, ArcSight, LogRhythm…).
ThreatSTOP’s ThreatLIST allows you to consume dynamically updated information about the threats targeting, or already present within your network.
ThreatLIST is easily configured to:
- Include the security policy categories meaningful to you.
- Integrate with your existing hardware and software platforms.
- Contain the desired historical and contextual meta data about IOCs.
There Standard ThreatList feature exports domain and IP IOCs in the policies of your choice. The DDOS ThreatList feature exports the IP IOCs available in the DDOS Targets.
Configuration summary
To enable and retrieve ThreatList exports:
- The feature must be enabled on your account by your ThreatSTOP sales representative.
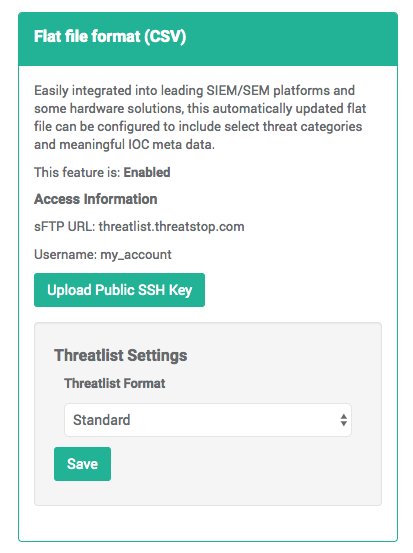
- On the SIEM integration page of the ThreatSTOP Portal
- Upload a public SSH Key (OpenSSH format or SSH2 format)
- Select the output format (Standard, Suricata, Domains)
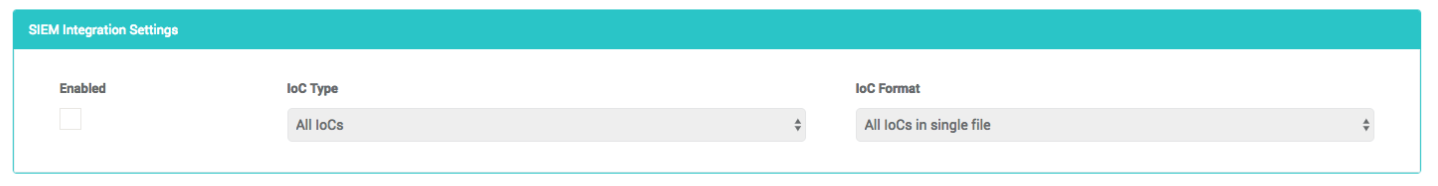
- Go to the settings page for the policy you want to export and select the Enabled checkbox under SIEM Integration settings.
- Access the policy file via sftp: the hostname and the account name are displayed on the SIEM integration page. Use the private key associated with the public key that you uploaded to authenticate. Files are published every two hours.
Access to this feature
Access to the ThreatList feature must be enabled in your product plan. The DDOS ThreatList feature is an additional add-on.
Please contact your ThreatSTOP representative if your current plan doesn’t include it.
Data Formats
ThreatSTOP SIEM integration is available in Standard, Suricata and Domain-Only formats.
- Standard files are in a CSV format. The format can be consumed by Splunk and includes the following data:
"IOC","Category","SubCategory","Severity","FirstSeen","LastSeen","Geo","IOC Type" -
Geo field is ISO-8859 encoded. All other fields are 7-bit ascii.
- Suricata files are formatted with one IoC per line with the following default format:
'alert ip [%ioc] any -> any (msg: "[%blocker_desc %blocker_type]"); priority: %priority; sid: %sid;)' - Domain-Only files are formatted with one IoC per line with only the domain. This format only works for DNS Defense policies with domain IoCs.
Enabling ThreatLIST
ThreatList files are generated from one or more of your custom policies. Enabling the feature is done in two steps:
- Step 1: configure the global settings for the feature.
- Step 2: configure the policy to be exported.
Step 1 - Global settings
- Navigate to the SIEM Integration tab in the navigation menu.
- Upload a public SSH Key (not your private key!). We support keys in the OpenSSH format and the SSH 2 format (e.g. generated with Putty).
-
Using the dropdown, select the desired format.
- If you’ve chosen Suricata, you will need to describe the format of the line. Our default is:
alert ip [%ioc] any -> any (msg: "[%blocker_desc %blocker_type]"); priority: %priority; sid: %sid;)
There are several variables that will be replaced with information about each indicator of compromise (IoC) when your file is generated:
- %ioc is the ip address from ThreatSTOP.
- %blocker_desc is the name of source of the block.
- %blocker_type is the type of threat.
- %priority is how dangerous the threat is.
-
%sid is an incrementing sid for suricata.
- If you’ve chosen Suricata, you will also be able to config the starting sid.
Step 2 - Policy settings (for Standard Targets)
- Browse to the policy configuration for each policy you want to export using ThreatList.
- Enable SIEM integration (Enabled checkbox).
- There are three configurations to set by choosing from the dropdowns.
- Set the Threatlist IOC Type. This determines what type of IoCs will be included in your SIEM file. Your choices are:
- IPs only.
- Domains only.
- All (both IPs and domains).
- Set the Threatlist Ioc Format. This determines if the system will generate separate files for each IoC type or a single file. Your choices are:
- Split IoC Types.
- All IoC Types in a single file.
- Save your changes.
Accessing the ThreatList files
Standard Targets
The ThreatLIST files are produced every two hours and are made available for you at threatlist.threatstop.com. The files need to be accessed via SFTP. Credentials will be provided by our support team.
The files following this naming convention:
threatlist-<policy_name>-<ioc type>-<timestamp>.csv
threatlist-<policy_name>-<ioc type>-latest.csv
where:
- Policy name is the name of the Policy being exported.
- ioc type is ip, domain, or all (for ThreatList setting requesting both IP addresses and domains).
- YYYYMMDD-hhmm is the timestamp at which the file was produced. The -latest file always points to the latest version.
For example:
threatlist-my_policy-ip-latest.csv
DDOS Targets
If your account is configured with access to the DDOS ThreatList feature, DDOS targets will be made available automatically on the SFTP server.
- The DDOS files are updated once a day
- They are posted in a directory named ddos in your SFTP account
- They follow the same naming convention as standard targets above. The IOC type is always ip.
- The DDOS policies are:
- drones
- memcached
- ntp
- resolvers
- snmp
- ssdp
- portmap