List types
User-Defined Lists are lists of IP subnets or Domains that can be added to a policy to block or whitelist them. User-defined whitelists take precedence over block lists (targets and user-defined block lists).
There are two types of user-defined lists:
- IP Lists contain IP subnets or IP addresses. IP Lists can be set to allow or block, to permit or deny connections to/from the IP addresses. Subnets are written in CIDR format (address/netmask)
- Domain lists contain DNS names - either FQDN (www.example.com) or wildcard names (*.example.com). Domain lists don’t specify an action; rather, they are associated with an RPZ Behavior when applied to a policy.
Each entries in both list types contain:
- The address (domain name or IP address)
- An optional expiration date, specifying when the domain or IP address should no longer be included in the policy.
- An optional comment, which may be used to indicated the reason for adding the list entry (such as an incident or trouble ticket number).
Lists are limited to 20,000 entries each. Note that customer policies may contain an unlimited number of User-Defined Lists.
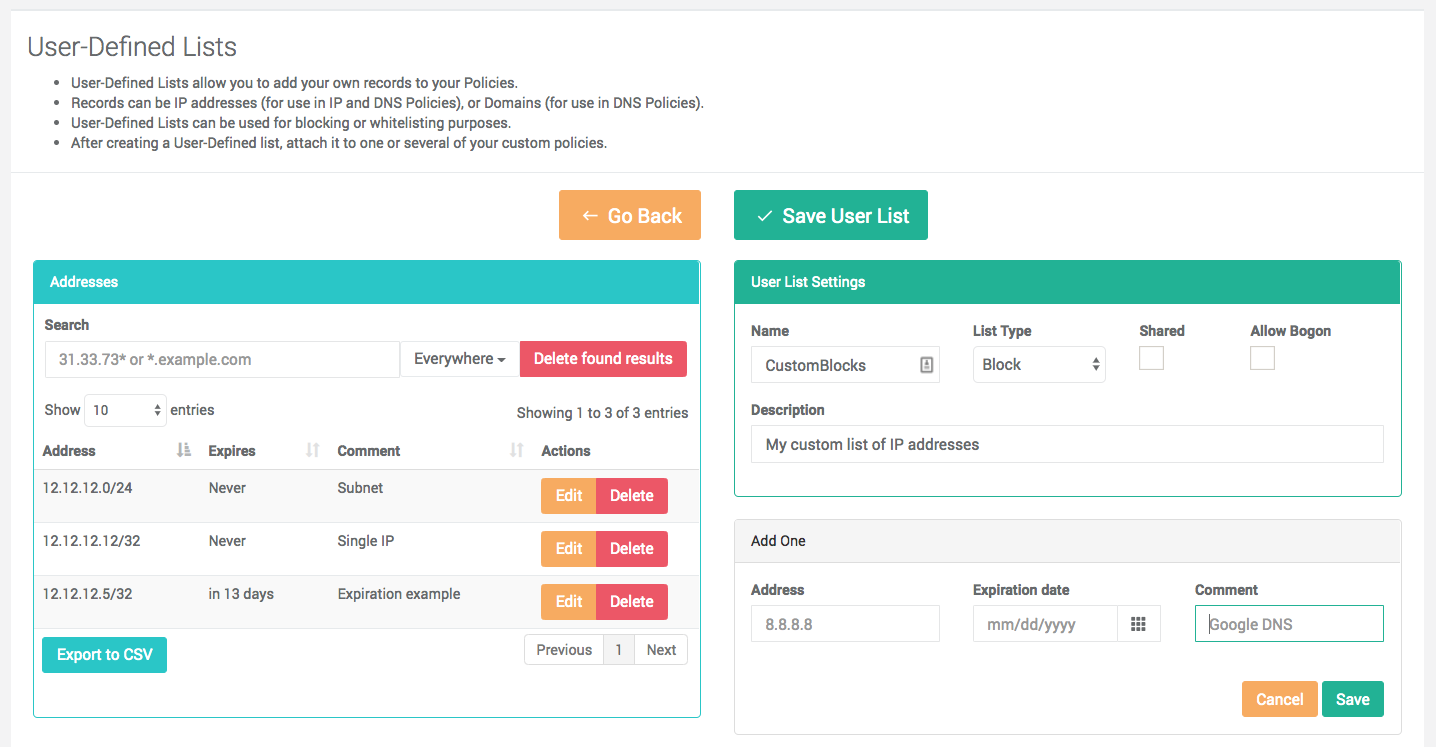
Editing a list
List configuration is located in the Configuration section of the Portal menu. After creating a list or clicking on the Edit link for an existing list, you will be presented with a page to add or remove entries.
- The left panel displays the current contents of the list
- The text search allows to search anywhere in the record, or to limit the search to the address, comment or expiration date fields.
- After searching for records, the Delete found results button can be used to delete all the records returned. If you delete the records by mistake, you can exit the page without saving to restore them.
- The right panel displays the settings of the list (see below) and two widgets to add new entries.
- The Add One widget is used to input new entries manually
- The Add Many widget is used to insert bulk entries, either manually or by pasting a list. The bulk insert will take a list of addresses, with an optional expiration date and optional comment separated by commas. You can include the address only, or skip the expiration date by leaving the field empty (address,,comment). The bulk insert widget can also be loaded with a list of addresses via a file upload, while optionally setting an expiration date for all new recprds. The file upload feature can also consume the output of the CSV export feature.
Export
The current contents of the list can be exported to a CSV file by clicking the Export to CSV button.
Validation
The edit screen performs the following validation:
- Subnets
- Valid unique IP address or Subnet (base address and mask)
- Subnet size is larger than > 8, to prevent user mistakes blocking very large numbers of networks
- No RFC1918 (private) IP address, unless the list is set to allow Bogons (see below)
- Domains
- Valid FQDN or wildcard record (starts with a star, star is not allowed anywhere else)
- Warning: Be careful with wildcards and TLDs to avoid over-blocking.
- Internationalized Domain Names are allowed in Punycode representation
Records can also be name servers records. Name servers records will block DNS responses that were provided by the DNS servers identified by the record.
- For IP addresses of DNS servers (e.g. a.b.c.d/32), the record must be written with the netmask, with 4 digits of the IP address written backwards, followed by the rpz-nsip suffix: netmask.d.b.c.a.rpz-nsip (e.g. 32.4.3.2.1.rpz-nsip). It is allowed to specify a subnet.
- For FQDNs of DNS Servers (e.g. host.domain.tld), the FQDN must be followed by the rpz-nsdname suffix: host.domain.tld.rpz-nsdname (e.g. ns1.example.com.rpz-nsdname).
Validation errors during a bulk import are displayed inline in the bulk data.
List settings
Sharing user-defined lists
The ThreatSTOP system allows sharing a user-defined list with other organizations. The account(s) with which the user-defined list is shared will be able to use the list in their policies, but not make changes to it. Lists that are shared with your account are displayed with a View (Read-only) button instead of the Edit and Delete buttons. To share a list, the Shared checkbox in the list settings must be on.
Shared UDLs are shared with account that have third-party access into your access.
To control the list of accounts that you share user-defined lists with, go to the User-Defined Lists > Sharing menu and add or remove organizations. The accounts in this list have access to all your shared UDLs.
Allowing Bogon IPs
Typically, blocking RFC1918 IPs should not be done as you run the risk of blocking internal traffic if it is routed through the device running ThreatSTOP.
It is possible that to create a User-Defined list with private IP subnets by checking the “Allow Bogon” box under User List Settings. A possible scenario for this feature is the following:
- You are using a policy that blocks IP traffic to a large subnet (for example, a Geographical target).
- But you want to allow one of your internal servers to initiate connections to IP addresses in that subnet that would be hard to list (e.g. mail servers).
- You can create a User-Defined (allow) list with the IP address of your internal server to allow it to connect, while the rest of your machines would not be able to.