Overview
The ThreatSTOP Roaming solution provides DNS firewall protection to endpoint users, even when they are not connected to their corporate network.
ThreatSTOP’s DNS and IP firewall services secure the boundary of a network and all devices on that network. ThreatSTOP Roaming protection secures individual Windows or OS X endpoints, allowing ThreatSTOP to protect these devices when roaming outside of your corporate network.
This document explains how to setup ThreatSTOP Roaming Devices in the portal and the Roaming client on your users’ Windows and OS X based devices. Additionally it explains how to integrate ThreatSTOP Roaming Devices into your network security profile. Finally, it will cover System requirements (OS and Hardware), and what DNS services are compatible with the system.
Portal Setup
Roaming setup is handled primarily through the ThreatSTOP Portal. Setting up a roaming device in the portal will generate a license key file that may activate a group of endpoint devices that share the same security policy. This key value will allow protection for the licensed number of protected devices. To purchase licenses for additional endpoints, please contact our Sales team (sales@threatstop.com). ThreatSTOP Roaming and ThreatSTOP’s DNS Firewall can share the same custom policies and lists. It also allows for rapid remediation of an endpoint by identifying the device by its hostname or serial number in the Roaming Report system.
Setting up a Roaming Device setup will require a DNS Firewall Policy. Please review DNS Firewall Policy Creation for more information.
The setup requires the following information about the endpoint client be provided to ThreatSTOP:
- Nickname: An easily recognizable name for the device being added.
- Hardware Identifier: Choose the hardware identification method your clients will use. The available methods are:
- Hostname: This is the hostname of the roaming device and is unique to each individual network. In Unix environments (and OS X) this name is displayed after the user name but in front of the command prompt on the CLI. Under Windows this can be discovered by right-clicking the Start button, selecting System and then looking for the Computer Name.
- Serial number: The serial number of the computer (Windows: wmic bios get serialnumber; OSX: system_profiler SPHardwareDataType).
- Hardware UUID: The Universally Unique Identified for the computer’s hardware (Windows: wmic csproduct get UUID; OSX: system_profiler SPHardwareDataType).
- Trusted DNS Servers: This field should be populated with DNS Servers you know to be trustworthy, generally servers inside your established network. If the Roaming client detects these addresses as the active DNS Servers it will consider itself to be “home” and therefore not “roaming,” and will retain the client’s DNS settings to the trusted server. If the device is removed from the trusted environment, or cannot access these IP addresses ThreatSTOP Roaming will enable itself based on its security profile. Multiple addresses can be entered with a comma between each entry.
- Require Admin: Set this to match your security policy. If your users can install, adjust, and maintain their own programs and have administrative rights to their machine it’s safe to set this to No. If your users are locked down and are prevented from installing their own software set this to Yes, as it will require a user with Administrative privileges to change the endpoint client. If this is set to No your users will not be able to Enable or Disable filtering, nor will they be able to add local whitelist entries.
- Location: Select the country your business is based in.
- Postal Code: Add the postal code (if available) of your business.
- Policy: Select the DNS Firewall policy you want to be applied to your Roaming clients. Predefined policies will populate the list by default, and user-defined lists can also be created for use with Roaming devices.
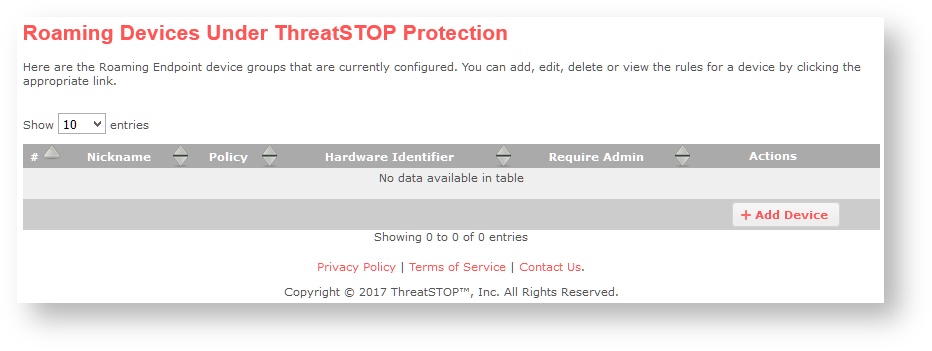
Roaming Devices
- Login to ThreatSTOP Portal.
- Click on Roaming Devices.
- If you are adding a new device click on + Add Device.
- The Add Device window will appear, you must provide this information:
- Nickname: An easily recognizable name for the device being added.
- Hardware Identifier: Choose the hardware identification for your clients.
- Trusted DNS Servers: Enter one or more IP addresses to DNS servers you know to be trustworthy. Multiple addresses can be entered with a comma between each entry.
- Require Admin: Set this to match your security policy. If your users have administrative rights to their machine it is safe to set this to No.
- Location: Select the country your business is based in. (Optional)
- Postal Code: Add the postal code (if available) of your business. (Optional)
- Policy: Select the threat policy you want applied to your roaming client group.
- Click on Next.
- Click on Finish. This will add the device to your account, and generate a key which will be used during Roaming Client Setup.
- Download the key by clicking on the key icon, and save this to a memorable spot on your hard drive.
Roaming Client Setup
There are two individual paths to installing Roaming (one for Windows, and the other for OS X) and we’ll cover them both. The general process is to login on an account with administrator privileges, download the installer to the system disk, run the installer, apply the license key, and enable Roaming Protection.
Roaming Protection Install Process - Windows
- Login to Windows.
- Download the Roaming client from: https://downloads.threatstop.com/pub/roaming/ThreatSTOP_Roaming_Installer.msi
- You can verify that the installer matches its digital signature. To do this:
- Right-click on the .msi file.
- Click on Properties.
- Click on Digital Signatures.
- Verify that the signer is ThreatSTOP, Inc.
- Double-click the installer icon.
- The installer will load and escalate to Administrator privileges if needed.
- Click Next.
- A permissions window may appear, click on Yes to allow the files to be copied into place.
- Click Finish. Once this is complete you’ll be ready to run the Roaming client.
- If this is your first time installing ThreatSTOP Roaming right-click the ThreatSTOP Roaming icon and click Run As Administrator.
- Click on the Settings tab.
- Click on Choose new key file…
- Browse to where the license key file was downloaded or saved.
- Select the file and click Open.
- Click on the switch icon to turn Roaming Protection On.
Roaming Protection Install Process - OS X
- Login to OS X.
- Download the Roaming client from: https://downloads.threatstop.com/pub/roaming/ThreatSTOP_Roaming_Installer.pkg
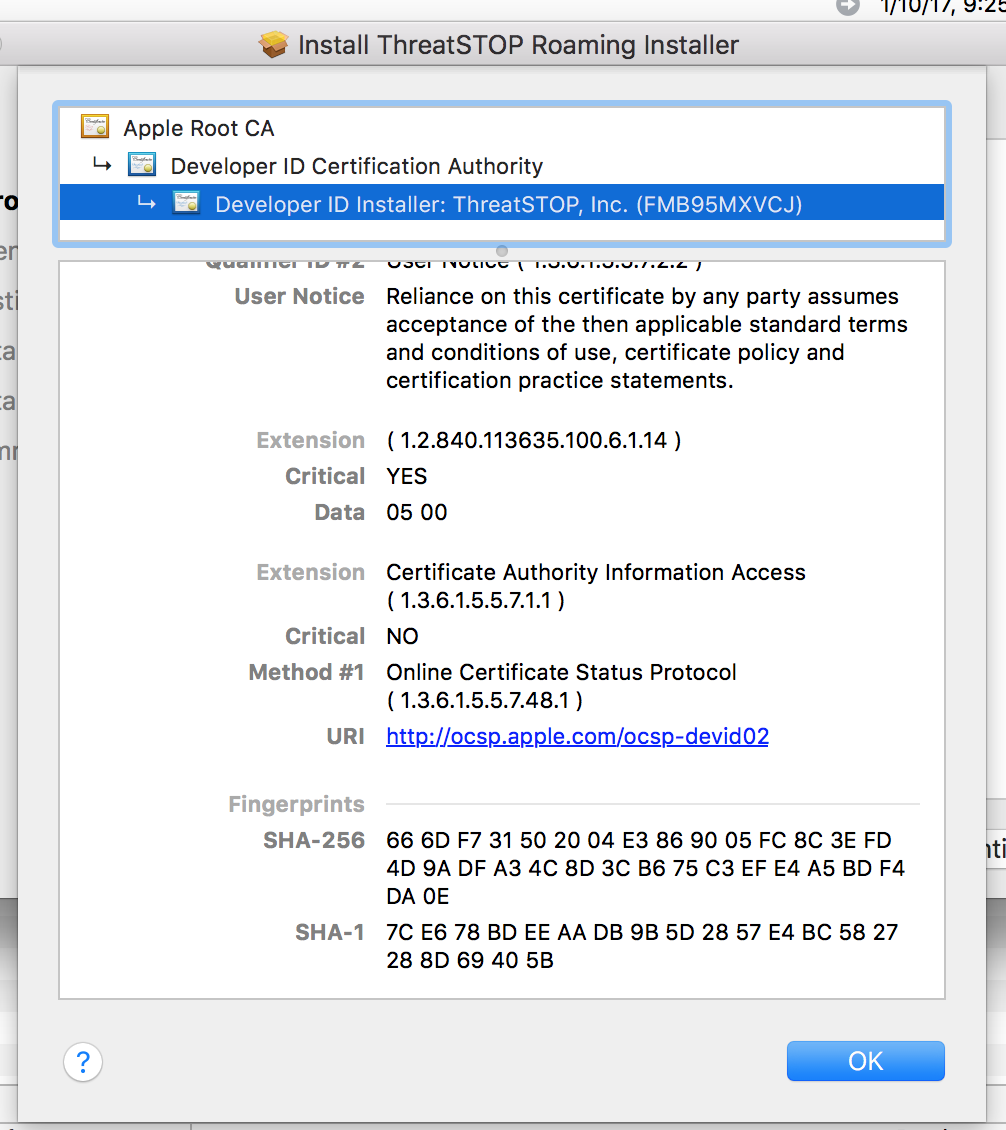
- You can verify that the package matches its digital signature:
- Start the installer
- Click on the lock icon in top right of the installer window
- Check the certficate - Developer ID Installer: ThreatSTOP, Inc. (FMB95MXVCJ)
- Continue past the software license agreement.
- ThreatSTOP Roaming must be installed to the system disk, click Continue.
- Click Install.
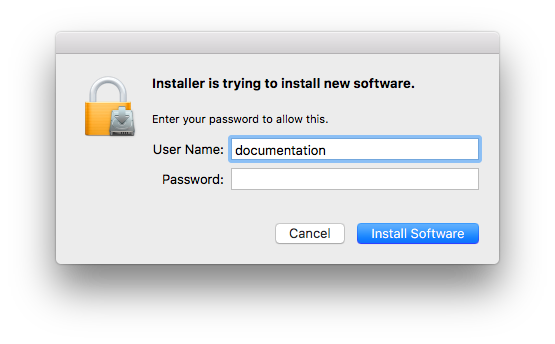
- You will be prompted for Administrator credentials to perform the install, provide the username and password, then click Install.
- This will copy the files to their installation location on your hard drive. Once this is complete you’ll be ready to run the Roaming client.
- Under Applications in the Finder locate and start the TSRoaming application to use ThreatSTOP Roaming on your device.
- Click on the Settings tab.
- Click on Choose new key file…
- Browse to where the license key file was downloaded or saved.
- Select the file and click Open.
- Click on the switch icon to turn Roaming Protection On.
Using the Client
The client maintains a mostly uniform interface between Windows and OS X, the one difference is the location of the menu bar. To keep things concise we’ll use screen shots from Windows, but the same options are available to OS X users. The client will appear in one of two modes:
 Non-privileged |
 Privileged |
-
As seen in the screenshots above non-privileged users can view their License, Device ID, the time their policy was last updated, and view events and actions taken by the client. They also have access to the entries in the menu bar which we’ll cover shortly.
-
Privileged users have full access to the client, can set allow lists, view events, turn the protection on or off, and also have access to the menu.
Menu
The menu contains three entries:
- TSRoaming: Provides access to the following sub-panels:
- About TSRoaming: Includes the program copyright notice, website, and support and sales contact information. You can also click Check for Updates to download and install the latest version of ThreatSTOP Roaming.
- System Info: Gathers system information relevant to ThreatSTOP support for the diagnoses of issues with the Roaming client. This is then broken down into four sub-windows:
- Diagnostics: Displays information related to your system properties, operating system, and other relevant diagnostic information for your system.
- Health Check: Runs checks on device connectivity, activity, and licensing to validate that the Roaming endpoint can talk to ThreatSTOP and receive configuration and threat intelligence data.
- Management Log: Displays a record of the log kept by the ThreatSTOP management service. This service monitors and controls the ThreatSTOP Roaming service daemon and ensures that the daemon is not interrupted in performing its duties.
- DNSD Log: Displays the logs kept by the ThreatSTOP Roaming service daemon in its duties. Including any connection difficulties and zone propagation issues.
- Quit: Exits the program.
- Edit: Allows the basic functions found in all office programs.
- Help: Help links back to this help documentation.
Report
The Report tab displays a breakdown of blocked communications over the last seven days as a pie chart. Each slice of the pie represents the threat level the communication attempt was deemed appropriate. In the example to the right we can see that three threat levels (5, 4 ,3) were blocked, and the number of attempts in each level are displayed in the middle of the slice.
Events
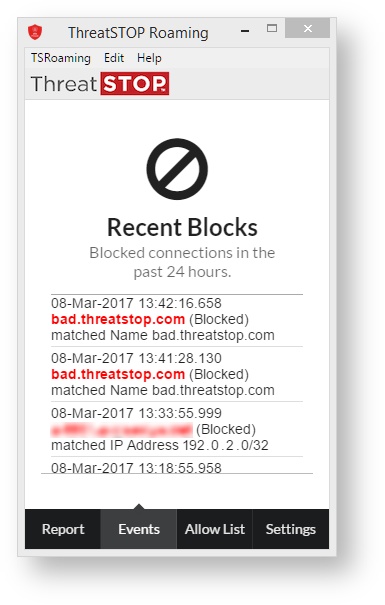
Events shows the date, and time at which a communication attempt to a site was made by the computer. It also denotes the action taken on that communication attempt based on both the global and local policy settings. Clicking on the address of individual entries will open a modal containing more information about the threat stopped. While not as detailed as the information provided by Check IOC in the web portal, the information here will give you enough of an idea to determine why we blocked a threat.
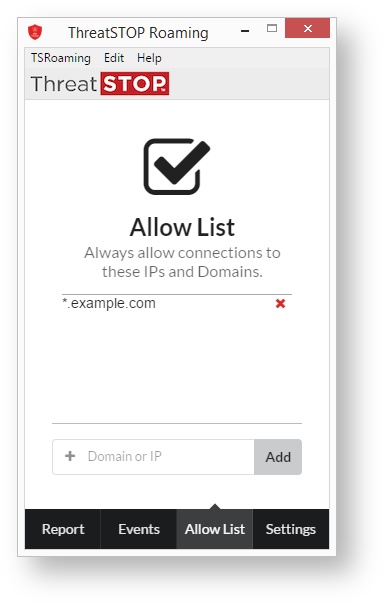
Allow List
The Allow List provides the ability for an administrator to provide a local override for records in the Threat Policy. Domain exceptions require at least a second-level domain. Entries that contain only a top-level domain (TLD) will be rejected. It is easy to unblock potentially harmful communications with this method.
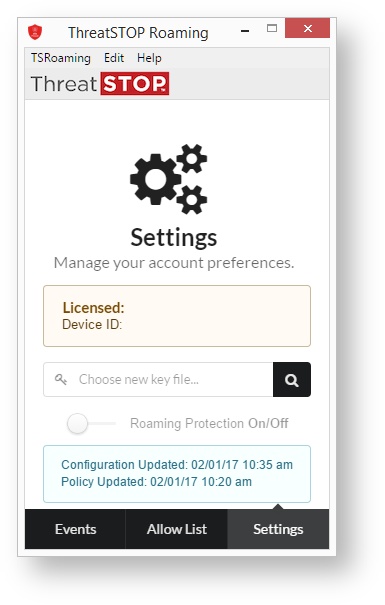
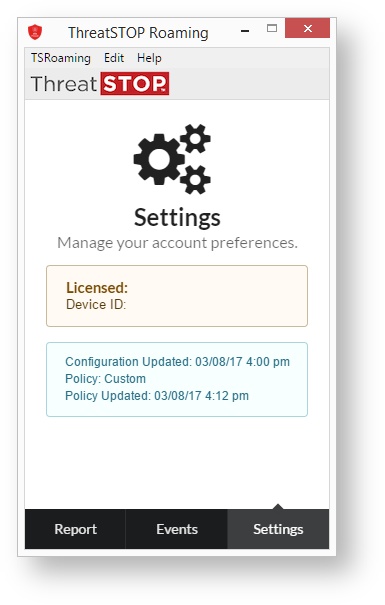
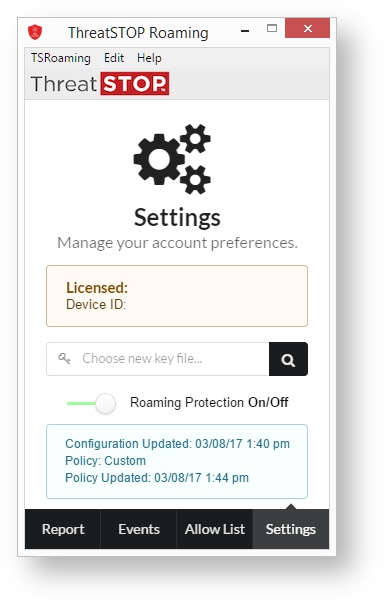
Settings
The final pane that is available to both privileged and unprivileged users is the Settings panel. The difference between the two is most clearly shown in the example above. The sample to the right shows the full display, and fields not available to unprivileged users will be marked:
- Licensed/Device ID: This field provides the ThreatSTOP account number associated with the license, and a Device ID.
- Choose new key file…: Clicking this allows for a new license to be associated with the Roaming client. (Privileged users only)
- Roaming Protection On/Off: This switch enables or disables ThreatSTOP Roaming protection on the device. When the switch is slid to the right the line next to it will turn green to indicate that protection is active. (Privileged users only)
- Configuration/Policy Updated: This box displays the last time a change was made to the configuration of the Threat Policy associated with the device, and the last time the Threat Policy was updated.
System Tray
After configuration it’s safe to close the ThreatSTOP Roaming window. The program will continue to run in the background and protect your system. In addition a system tray icon will appear, this will show the blocking status of ThreatSTOP Roaming.
Clicking the icon will re-open the main control window, where right-clicking (or Control-clicking on OS X) will allow the program to be activated/deactivated and other functionality to be used.
Administration
License Keys
After a device is successfully setup a unique license key will be created for a group of endpoints. The key represents the licensed number of endpoint devices. Once the maximum number of endpoint devices is reached, or if multiple policy groups are needed, you must purchase one or more additional keys.
After the key is associated it will take up to 30 minutes for the Threat Policy to populate to the Roaming client, after which your device will be protected by your chosen policy.
Automated Installation
For assistance with automated installations please contact ThreatSTOP Support.
Uninstall
Uninstalling the Roaming client is OS dependent. OS X uses a dedicated uninstaller, while Windows relies on the operating system’s uninstall routines.
On OS X, use the uninstall program to remove the program and the setup and config files. We do not recommend dragging the icon to the trash.
On Windows, the program must be uninstalled through Add Programs or Features.
Upgrading
Upgrades can be run with the current version in place. Simply download the newer version and run the installation again.
User Defined Lists
User defined lists for ThreatSTOP Roaming Devices can be administered through two points:
- Globally (through the portal)
- Locally (on the device itself)
End-users cannot adjust assigned policies, either locally or globally, without Administrator rights.
Global (Portal)
Global policy administration is handled through the Roaming Devices section of the ThreatSTOP portal. Established devices will be listed here with a drop down menu that allows the user to select the policy that best fits their needs on the endpoints for their device. Each device may have a unique policy established for their endpoint devices. Changing the drop down to a new policy will update the policies used on these devices.
Local (Roaming Device)
On the endpoint itself the policy may be modified to include a whitelist. This change will not be reflected upstream in the portal, and the only way to affect this change is for a user with local admin privileges to change the policy when the device is set to Admin: Yes in the portal.
Reporting
Reports for ThreatSTOP Roaming are covered in Roaming Reporting.
Requirements
Operating System
ThreatSTOP Roaming is compatible with these Operating Systems:
- Mac OS X
- Yosemite (10.10)
- El Capitan (10.11)
- Sierra (10.12)
- High Sierra (10.13)
- Microsoft Windows
- 8.1 and 10
- .NET framework 4.5.2 or above
Hardware
Your device must meet or exceed these hardware requirements:
- CPU: No requirement beyond the ability to run the parent OS.
- Memory: Dependent on policy size (estimated at 50 MiB/100,000 entries in policy)
- Disk: 300 MB disk space for installation
Network Connectivity
To function properly, the application must have access to the following:
- DNS over TCP
- IP range: 192.124.129.0/24
- TCP port 53
- DNS over TLS
- hostname: ts-ctp.threatstop.com
- IP range: 204.68.97.208/28
- TCP port 5353
- HTTPs
- Hostname: rest.threatstop.com
- IP range: 204.68.99.208/28
- TCP port 443
Compatibility Issues
Some minor compatibility issues have been discovered between ThreatSTOP Roaming and this software:
-
DNS Crypt - DNS Crypt takes control of the operating system’s DNS settings. This prevents ThreatSTOP Roaming from successfully communicating with ThreatSTOP’s servers.
-
OpenVPN Connect (earlier than 2.0) - OpenVPN Connect works by taking control of the operating system’s network stack and pointing DHCP and DNS resolvers to trusted hosts inside a different network. This will override ThreatSTOP Roaming’s behavior and can create a conflict. To work around this, ThreatSTOP roaming uses the Trusted DNS Server setting to establish when to disable itself. Setting the address for the DNS server that OpenVPN Connect uses will turn off ThreatSTOP roaming and instead rely on the parent network’s security services.
-
Hyper-V - Due to how Hyper-V’s Virtual Network Switch handles interfacing with the parent OS, ThreatSTOP Roaming can only be used on systems on which Hyper-V has been installed, and a Virtual Network Switch has been setup in Private or Internal modes.
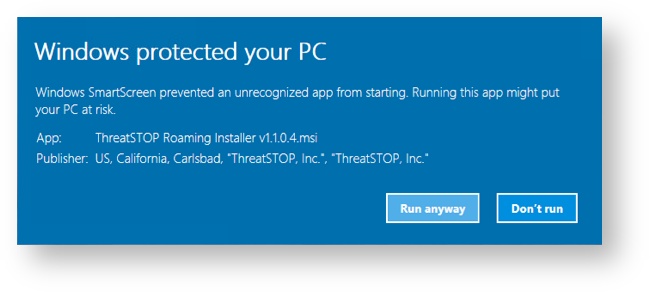
- SmartScreen Warning In rare instances some Windows 10 systems can display a SmartScreen Warning on app installation. Provided that the digital signature checks out, it is safe to allow the installation program to run. If you see this screen please contact ThreatSTOP Support (support@threatstop.com). To continue installation:
- Click More Info.
- This will present application and publisher info.
- Click Run anyway.
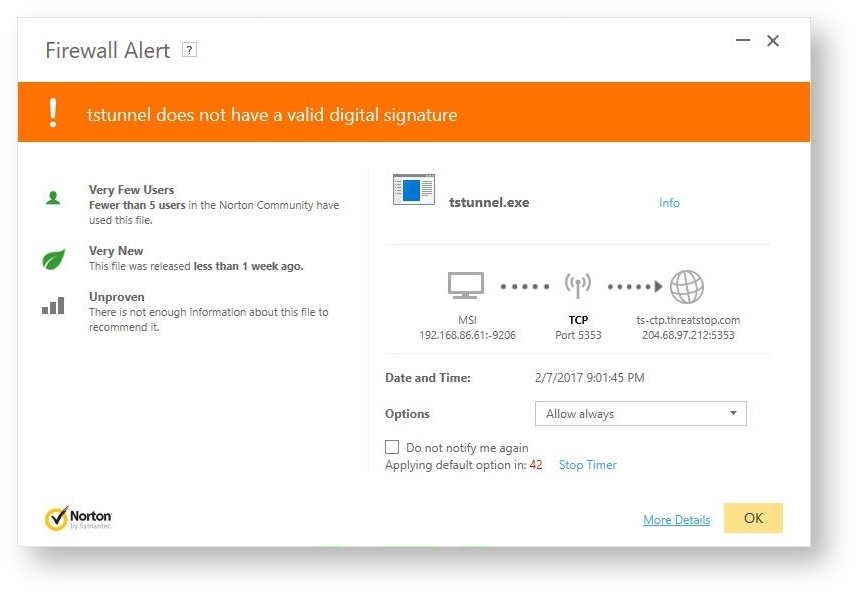
- Anti-Virus Warnings Some anti-virus tools will throw issues based on their internal settings. To date these issues have been noted during our testing:
- Norton Anti-Virus: May throw warnings that program is in limited use by Norton’s user base.
- ESET: When set to Paranoid mode, ESET will ask if ThreatSTOP Roaming should be allowed to connect to the Internet.
It is safe to set exceptions for these warnings, not doing so will prevent ThreatSTOP Roaming from operating as intended.
Protecting Virtual Machines
Virtual machines running inside a vmhost protected by ThreatSTOP Roaming Defense are filtered if they configure to use the host’s network. If they are connecting directly to the network (e.g. VirtualBox’s Bridged mode), they will get make DNS requests directly without being filtering by the Roaming Defense protection.