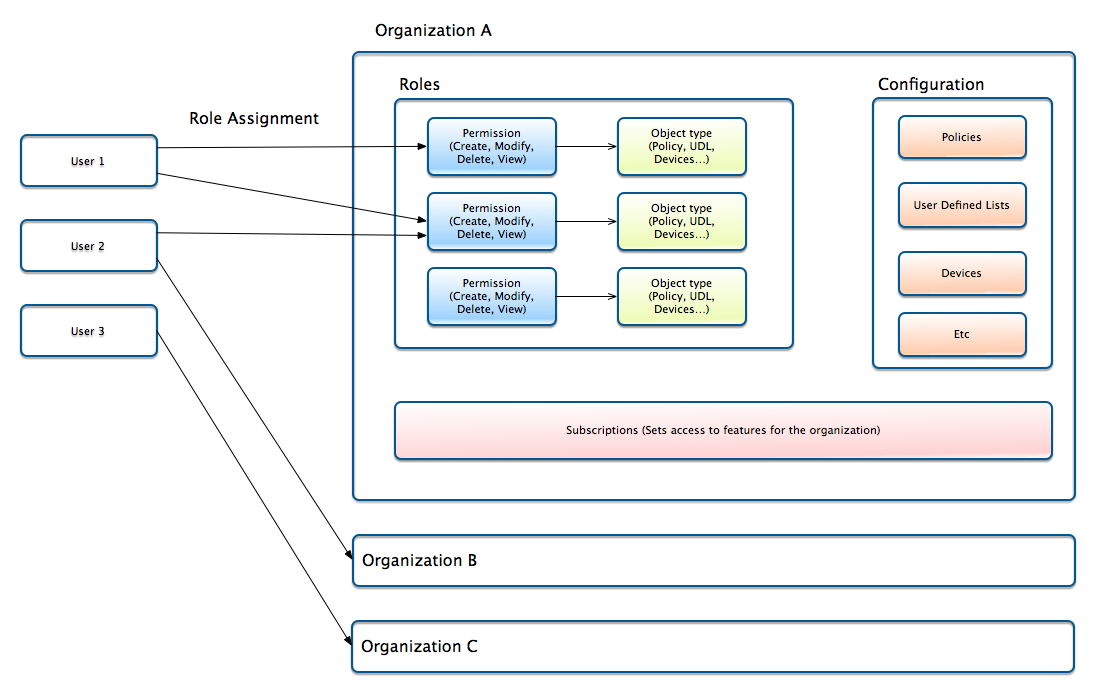
Role-Based Access Control
Starting with version 6, the ThreatSTOP Admin Portal supports multiple users and Role-Based Access Control within an organization account.
- Users are identified by their email address.
- Organizations are the entity which contain configuration settings: policies, devices, user-defined lists…
- Users can login into one or multiple organizations.
- The level of access is customizable for each organization and user.
Multiple organizations and users
- Users with access to multiple organizations can select which account they will access during the login operation. A default organization can be set at the same time.
- After logging in, the current organization being access is displayed under the user’s name and avatar. users can switch the organization they are managing by clicking on the organization name and selecting from the list of organizations they have access to.
- Users can change (or unset) their default organization while switching to a different one. The setting is set in the Organization Switch (see below).
Every organization account is identified by its ID. The ID of the organization that a currently is logged into is displayed in the menu, under the user name and icon.
Roles
Roles define the operations that users can perform in a given organization. Roles are groups of permissions to access ThreatSTOP features and a user can have a combination of roles in the same organization. Permissions are always additive: if users has multiple roles assigned in the current organization, they will have all permissions enabled across these roles.
The Admin Portal defines a set of predefined roles. Accounts with the Advanced RBAC SKU also have the ability to customize roles.
To access the role management page, click on the Roles entry under the Configuration menu.
- Permissions
The following operations are available by default to all accounts:
- View and edit a user’s own settings (name, email address, authentication settings, portal preferences)
- View the list the policies, devices and user-defined lists available in the account (read-only).
The following permissions are available:
| Object | Operation | Description |
|---|---|---|
| Organization | Manage organization settings | Change organization settings - name and address |
| Devices | Manage Devices | Perform all operations on devices - creation, delete, change policy and settings |
| Devices | Manage device settings | Change settings but no ability to create/delete devices |
| Policies | Manage Policies | Perform all operations on policies - creation, delete, change targets and user-defined lists |
| Policies | Manage policy settings | Can change content of policies; no permission to create or delete policies |
| User-Defined Lists | Manage UDLs | Perform all operations on UDLs; add, delete, change contents |
| Reports | View reports | Run reports |
| Email reports and alerts | Manage Reports | All operations on email reports and alerts |
| ThreatList | Manage SIEM Integration | Can change all ThreatList settings |
| Check IOC | Access Check IOC | Lookup IOCs in the Threat Intelligence database |
| API Keys | Manage API Keys | Perform all operations on API keys - create, delete, set permissions and settings |
| API Keys | View API Keys | Can list the API keys: tokens, permissions and settings |
| Log files | Upload log file | Ability to upload log files via the Admin Portal |
| Users | User Management | Ability to invite users, remove users, change role assignment for users |
| Roles | Role Management | Ability to manage roles - create, delete and change permissions |
You can create custom roles by combining permissions via the Role Management entry in the menu (SKU required).
The default roles are:
- Full Admin: Access to all configuration changes: Manage organization settings, Manage Devices, Manage Policies, Manage User-defined Lists, View reports, Manage reports, Manage SIEM Integration, Manage API Keys, Manage Users, Manage Roles. The system must have at least one user with the Full Admin role.
- Report and Policy Viewer: Read-only access to policies and user-defined lists settings, plus access to reports.
- Report and Policy Manager: Editing of policies and user defined lists, plus access to reports.
- Reporter: View reports and access to Check IOC.
- Help Desk Manager: Manage user defined lists plus access to reports.
All predefined roles also have access to the CheckIOC features.
Organization switch
For users that a role in multiple organizations, the organization can be selected at login time or using the Organization Switch. During login, after validation credentials (user, password and two-factor authentication if enabled), the portal will present users with the list of organization they have access to (unless the user set a default organization.)
The Organization switch is reached by clicking on the Organization ID at the top of the menu. The Account switch displays the list of organizations that the user can switch into. The role(s) assigned to the user are shown when selecting the organization. The Organization switch can also be used to set or clear a default organization, which will be used during login.
Management user interface
The Role Management page displays:
- a list of roles, which can be edited by on them
- a list of users with a role in the organization
Users might have the Manage Users or Manage roles permission to access this page.
Role Management
The following operations are available to manage roles:
- Create new role. Custom roles require the Advanced RBAC SKU. Organizations with this SKU can create an arbitrary number of roles. Roles have a name, a description and a list of permissions selected on the role creation page.
Click on a role to reveal a menu with the following operations:
- Edit permissions: list the permissions associated with the role. Organization with the Advanced RBAC SKU can edit the permissions for custom roles. Predefined roles cannot be changed. For accounts without the SKU, the permission list is read-only.
- View users: show a list of all users with the selected role.
- Delete role: delete the current role. This operation cannot be reversed. A role can only be deleted if no users are currently assigned that role, and if the role is a custom role.
Role assignment
To assign and unassign roles for an existing user, select the user in the User List (top right). The list of roles currently assigned to the user will be displayed in the Assigned Roles list. The roles that are available but not assigned to the selected user are listed under Available Roles.
To assign a role to the selected user, drag the role from the Available Roles list to the Assigned Roles list. To unassign a role, drag the role back to the Available Roles list. Changes must be saved (Save button) and take effect the next time the user logs in.
The Reset button will revert unsaved changes made to the user’s role.
From this screen, you can also remove a user, which will remove him/her from the list of users with access to the organization (this has no impact on other organizations that the user may have access to).
New users
If you want to grant a user access to the organization, click on the Add User button.
- You will be prompted for the email address of the user and the roles to assign to the user. The roles can be changed after the user accepts the invitation to join the organization.
- If the email address is already associated with a user account in the ThreatSTOP system, the user will receive an email notification to accept the invitation. Upon clicking a link in the email, their access will become active.
- If the email address is not already associated with a user account in the ThreatSTOP system, an email will be dispatched to invite the user to register an account first. Once the registration is completed, their access will become active.
Audit Log
With several users able to change configuration settings, changes are logged and available via the Audit Log feature, reached via the menu entry of the same name.
The Audit Log page reports the following:
- The time of the change
- IP address that originated the change
- Who originated the change - either a user in the portal (identified by the email address), or a direct API call made with a an API key (the audit log will show the last 6 digits of the API key)
- The operation (created an object, edited an object, or deleted the object)
- The name of the object; if the object was renamed during an edit, the new name will be displayed.
Changes are tracked for the following objects: devices, policies, use-defined lists, users and roles, organization settings, API keys, Customer networks, Email Reports and ThreatList settings.