Overview
ThreatSTOP DNS policies are implemented using Response Policy Zones (RPZ). This currently includes ISC BIND servers and derivative products, as well as the Unbound DNS Server. Microsoft DNS Server doesn’t support RPZ actions and is limited to returning NXDOMAIN responses.
RPZ defines a DNS zone format which provides a mechanism to override the DNS server’s responses by applying policy actions to triggers (such as the queried DNS name, or the IP addresses in the response).
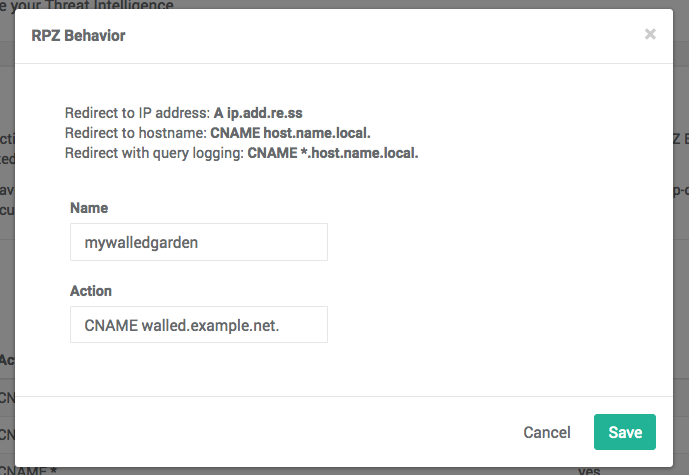
RPZ Behaviors provide a mechanism to assign specific RPZ policy actions to individual targets and custom lists within a ThreatSTOP DNS firewall policy. ThreatSTOP provides a default set of RPZ behaviors as well as the ability to define customized behasviors. Typically, adding a custom behavior can be used to redirect traffic to a walled garden by overriding the response of the DNS server.
Default RPZ Behaviors
Default RPZ behaviors are managed by ThreatSTOP and available to every account. They can not be edited. The list of default behaviors is the following. Typically, policies use the NXDOMAIN action.
| Name | RPZ Action | Description |
|---|---|---|
| NXDOMAIN | CNAME . | Return NXDOMAIN to the client, indicating that the requested name doesn’t exist. |
| NODATA | CNAME .* | Return NODATA to the client, indicated that there is no record of the requested type for the requested name. |
| PASSTHRU | CNAME rpz-passthru. | Queries for this record will be allowed, regardless of other RPZ rules. They will be logged as well. |
| DROP | CNAME rpz-drop. | Don’t reply to the client. May cause client to try another resolver. |
| GARDEN | CNAME garden.threatstop.com. | Example of a walled garden behavior. |
Custom behaviors
Custom RPZ behavior follow the syntax from the RPZ RFC, e.g.
- CNAME garden.example.com. : Resolve record to garden.example.com (note the required trailing dot).
- CNAME *.garden.example.com. : Prepend queries name to walled garden DNS name.
- A [IP address] : Resolve record the specified IP address.
Using a wildcard action (e.g. *.garden.example.com.) will result in prepending the DNS name originally requested (e.g. bad.threatstop.com.garden.example.com.). Used in conjunction with a walled garden, this can be used to capture the original requested DNS name, for example by capturing the logs of the DNS server, or as the Host header of an ensuing HTTP request.