This documentation is available in PDF format in the ThreatConnect’s GitHub repository.
Introduction
The ThreatConnect Platform is a security platform which includes a Threat Intelligence Platform (TIP) to collect and manage IOCs (Indicators Of Compromise) and Security Orchestration and Response (SOAR) capabilities.
The “Active IOCs” integration between ThreatSTOP and ThreatConnect automates the import of the IOCs from ThreatSTOP Policies into the ThreatConnect TIP. This provides users with the ability to:
- Browse the IOCs in their current ThreatSTOP policies and view their meta data.
- Leverage their ThreatSTOP Policies in ThreatConnect playbooks.
Features
The integration allows users of both platforms to select one or multiple ThreatSTOP policies and import their IOCs in the ThreatConnect Platform. The IOCs are imported hourly as ThreatSTOP policies are updated.
Data Mapping
Targets are ThreatSTOP’s atomic building blocks for policies, typically grouping IOCs by the associated threat. Each IOC is imported with the following data:
| ThreatSTOP field | ThreatConnect field | Description |
|---|---|---|
| Target name | Associated Intel | |
| Threat Type | Tags | The Threat Type associated with the target |
| Severity | Threat Rating | The ThreatSTOP severity score (0 to 5) |
| Confidence Level | Confidence Rating | The ThreatSTOP scale (1-5) is translated to a range from 20 to 100 |
| First and Last Seen | First and Last Seen | The first and last time the IOC was in ThreatSTOP targets preset in the exported policies |
| N/A | Added | The first time the IOC was imported |
| N/A | Last Modified | The last time the IOC was imported |
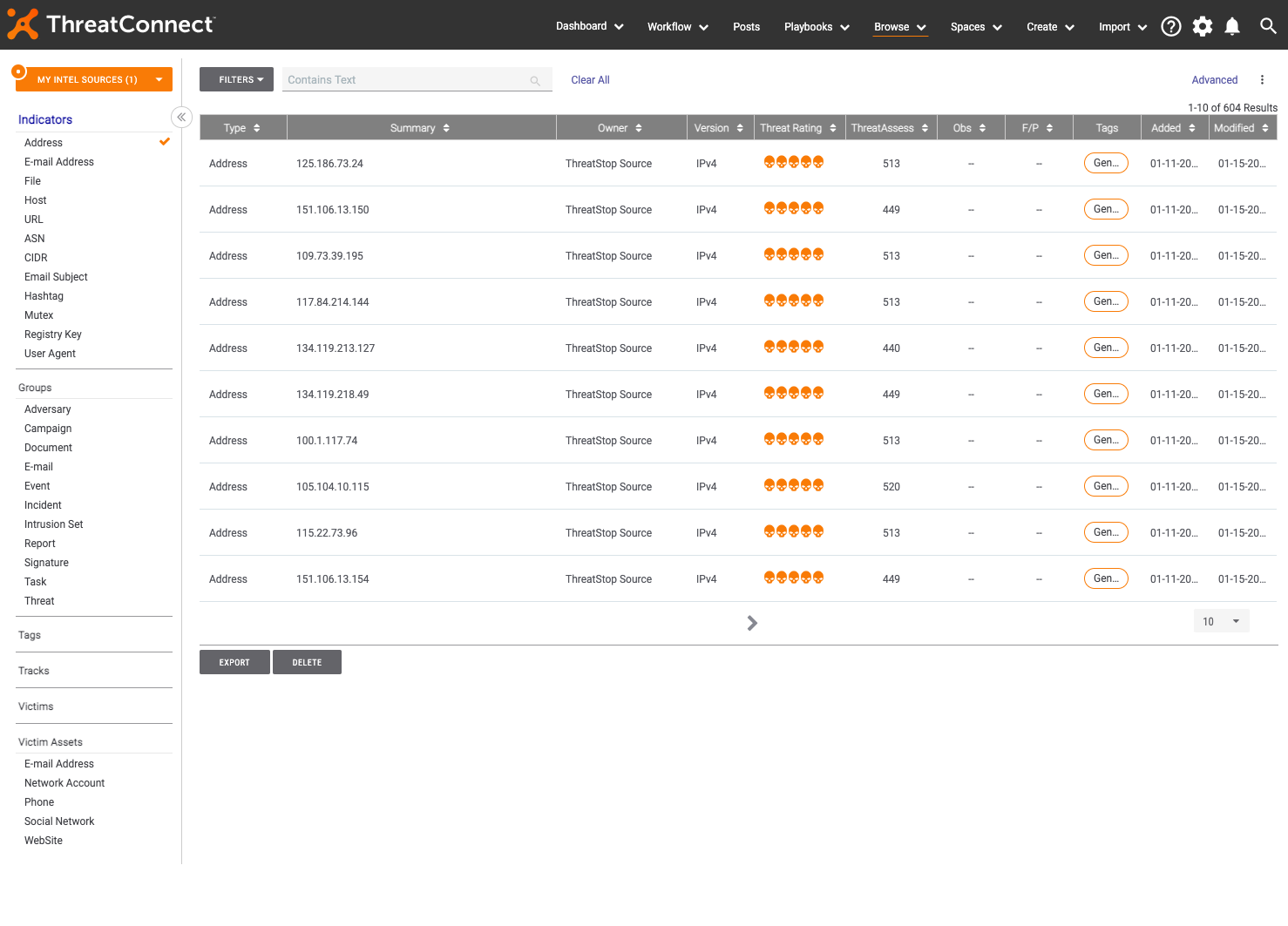
Example of IOCs imported from ThreatSTOP into ThreatConnect:
IOC Details:
IOCs are imported as one of three ThreatConnect IOC types:
- Addresses (v4 IP addresses).
- CIDR (v4 subnets).
- Host (FQDN and domains).
An IOC can be present in multiple ThreatSTOP Targets; the IOC will show meta data for each target. The highest severity and confidence scores across all targets are used.
Policy Action
For IP policies, the IOCs exported to ThreatConnect are the Block section of the polices; the Allow section is not exported. For RPZ policies, IOCs are exported for every RPZ action except Passthru.
Exceptions
The following elements of a ThreatSTOP policy are not imported into the ThreatConnect TIP:
- ThreatSTOP IOCs for wildcard DNS domains (e.g. *.example.com).
- ThreatSTOP targets with a severity score of 0 (used for whitelisting and Geographical targets).
- IP addresses and domains from User-defined lists.
Browsing ThreatSTOP IOCs in the ThreatConnect Platform
IOCs are displayed by following the Browse > Indicators menu and selecting Address, CDIR or Host. Types can be combined using the Indicators list in the left menu.
- If you are using ThreatConnect’s shared environment, the IOCs imported are attached to a source named ‘ThreatSTOP’. In a private instance (cloud or on-premise), the source name is set by the user during the installation.
- In the details tab of the IOC, the Associated Intel section will show the targets that the IOC is (or was) present in. You can click on each of the target to access a page with the description of the target and the list of IOCs in it.
- The associated indicators section lists the IOCs in the same ThreatSTOP target.
- The list of targets can be accessed by following Browse > Groups > Threat. The integration only includes targets present in the ThreatSTOP policy.
- The list of Threat Types can be accessed from the Tags left menu of the Browse IOC page. Only Threat Types associated with IOCs in the policy are imported.
Maximum Policy Size and Deprecation
IOCs imported using the integration will be deleted according to the deprecation rules set for the ThreatSTOP source. Deprecation rules must be configured to avoid reaching the maximum number of IOCs allowed in the ThreatConnect Platform (500,000 per source). If an IOC remains in the ThreatSTOP targets, it will be refreshed and its deprecation value reset. ThreatSTOP recommends deprecating the IOCs to be deprecated overnight days, i.e. deprecating IOCs by 100 points daily.
The integration module will stop importing IOCs if the combined size across the policies reaches 500,000. Users should consider this limit and the size of the ThreatSTOP policies they choose to import when customizing deprecation rule, so as to avoid reaching the limit.
Configuration
Requirements
ThreatSTOP accounts require two features to be enabled on the account:
- Custom policies
- ThreatConnect integration
Please contact support@threatstop.com if you wish to use the integration but your account doesn’t have the required feature.
The ThreatConnect account requires an API user to install the application.
Setup
The integration is configured into three steps: first selecting policies to import using the ThreatSTOP Portal, download the TCEX application and finally configuring the integration key in the ThreatConnect Platform.
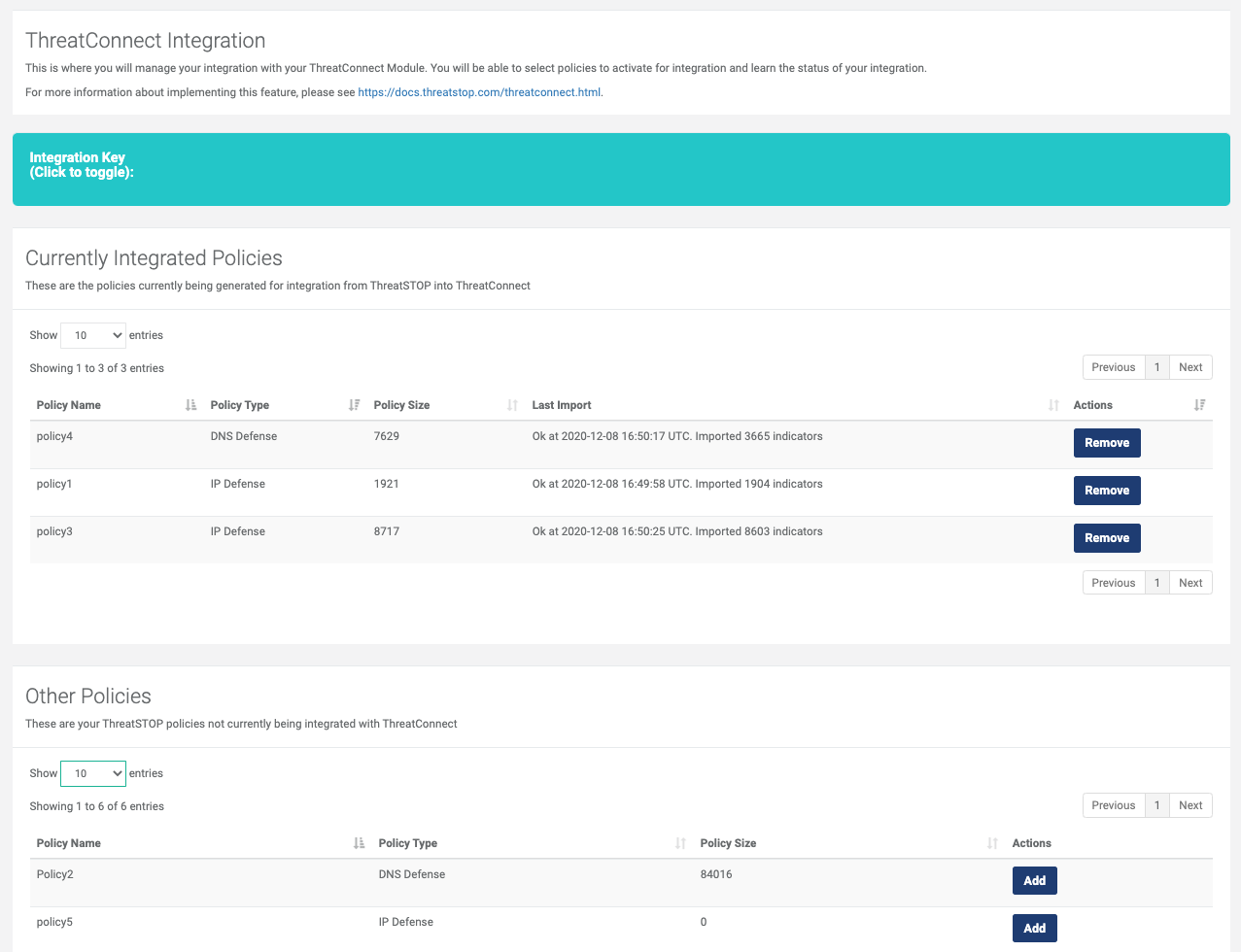
- ThreatSTOP Portal
- Login to your ThreatSTOP Account.
- Browse to the Integrations > ThreatConnect page.
- You will be presented with a list of your custom policies.
- Click Add to add a policy to the list of policies to be imported. The policy must be a custom policy; pre-defined policies can’t be exported.
- It will take a few minutes (less than 5) for the policy to be available to ThreatConnect.
- The Integration Key which is used in the next step is shown at the top of the page.
- Download the application
- Retrieve the TCEx file from ThreatConnect’s GitHub repository
- ThreatConnect Dashboard
- For general documentation about adding an application, please refer to the ThreatConnect System Administration Guide (Install an App). For more information, contact your ThreatConnect Customer Success representatives.
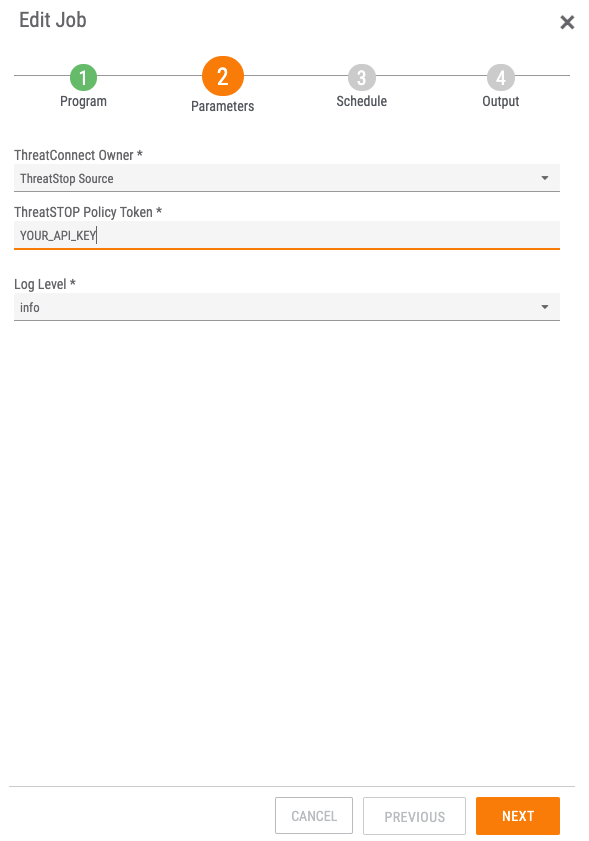
- Step 1: enter the ThreatConnect Owner (ThreatStop source), API Key (retrieved from the ThreatSTOP Admin Portal) and log level (recommended value: info)
- Step 2: select how often the integration will run (i.e. check for new data and import it). The recommended value is every two hours.
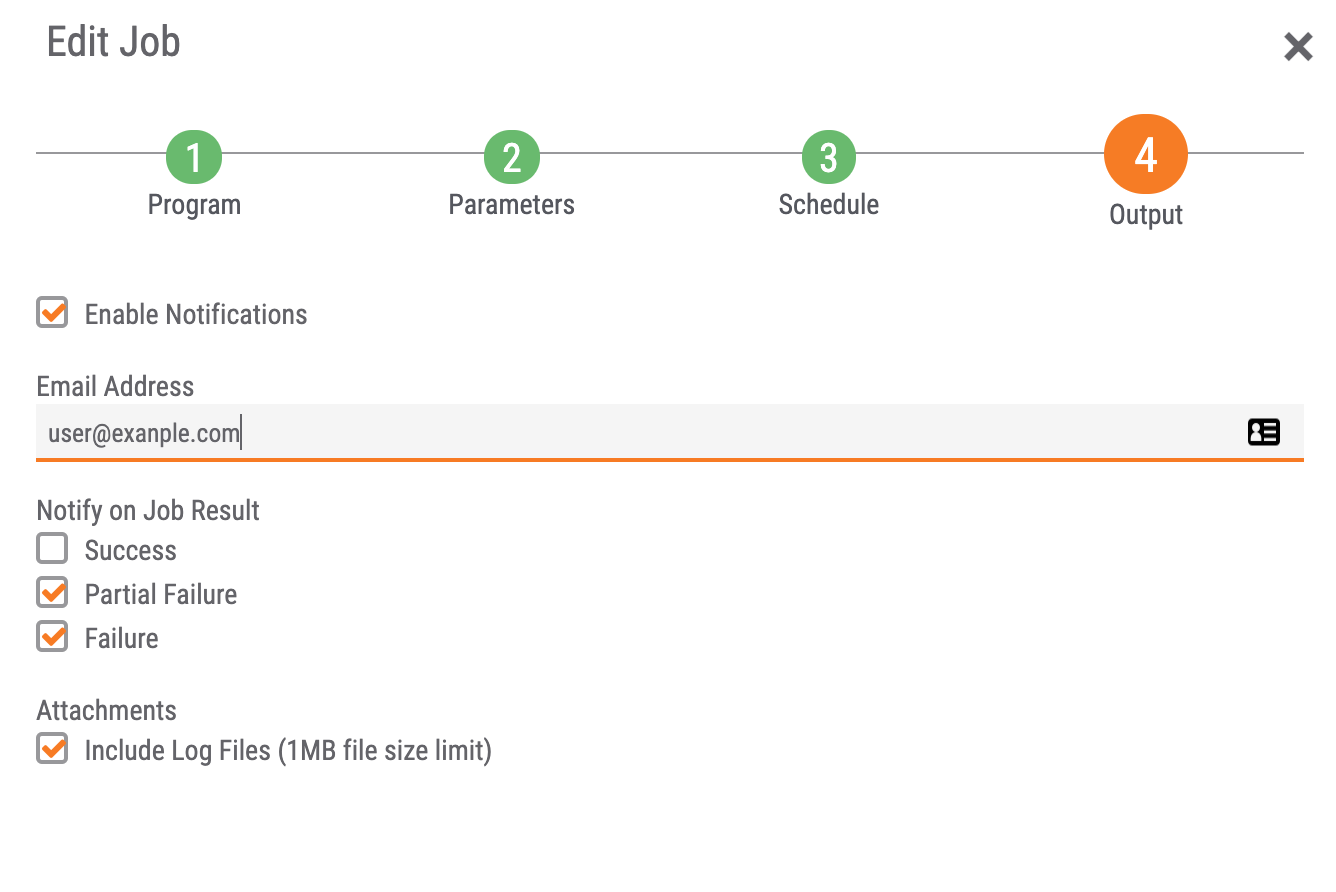
- Step 3: set the desired notifications. The recommended setting is to alert on failure and partial failure.
STEP 1
STEP 2
STEP 3
Schedule setting
The default schedule setting for importing the latest policy is every two hours. This setting controls how often the ThreatConnect Platform will check for updated policies. Imports are performed only if at least one of the selected policies has been updated.
The frequency can be increased based on the policy sizes. The following table lists recommended frequencies based on the total size of the selected policies.
| Combined size of policies | Recommended frequency |
|---|---|
| 50k to 100k records | Every 15 minutes |
| 50k to 100k records | Every 30 minutes |
| 100k to 400k records | Every 45 minutes |
| 400k to 600k records | Hourly |
Configuration changes
- Additional policies can be added to the list of exported policies.
- Policies can be removed from the list as well. IOCs will be deleted from the ThreatConnect database according to the deprecation rules.
- Policies are refreshed hourly by the ThreatSTOP system; the ThreatConnect application will import the policy based on the frequency selected in step 2 above.
Integration status
- The configuration page in the ThreatSTOP will display the update time for every exported policy and the number of IOCs in the last export. It will also warn if a policy has not been retrieved in more than one day or if the combined size of the policies exceed the maximum import size.
In the ThreatConnect Dashboard:
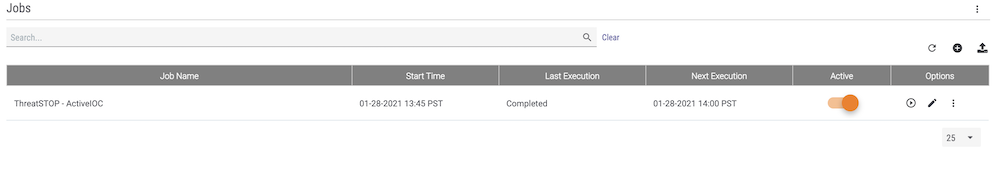
- The status of the last import attempt (Completed or failed) is shown on the Application list page
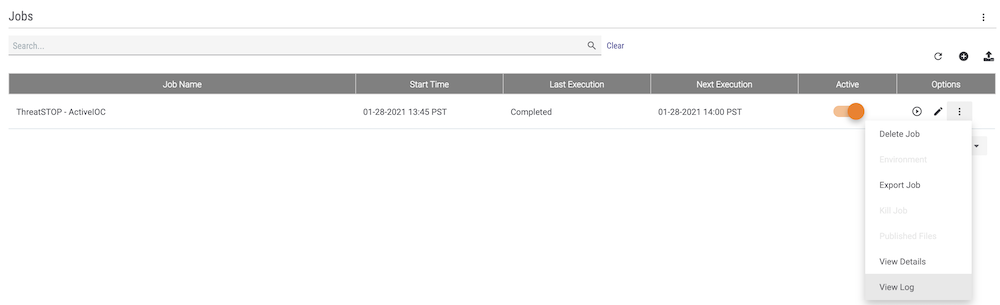
- The Log for the integration can be viewed or downloaded by selecting View Log on the ThreatSTOP Integration entry.
- Possible errors include an incorrect Integration Key or exceeding the maximum number of IOCs that can be imported.
Threat Types
The ThreatSTOP Threat Types associated with targets are mapped to Tags in the ThreatConnect Platform. The possible values are:
- Anon Proxies
- APT
- Crawlers
- Botnet
- C2
- Cryptomining
- Exfiltration
- Exploit Kits
- General
- Geo
- Inbound Attacks
- Infection Sites
- Malware
- Phishing
- Policy Violations
- Ransomware
- Scams
- Scanners
- Sinkholes
- Spam
- Test Target
- Whitelists
ThreatSTOP Support
Please contact ThreatSTOP support for assistance with using the integration.
Release notes
| Version | Date | Changes |
|---|---|---|
| 1.0.4 | February 2021 | Initial release |