Policies define the set of IP addresses or domain names (i.e. IOCs, or Indicators of Compromise) that will be applied to the device to block malicious IP traffic and DNS lookups, or to allow whitelisted IP and DNS traffic.
Policies are assembled with:
- Targets: ThreatSTOP tracks IOCs and groups them as objects named targets. Targets can contain IP Addresses, subnets, DNS domains, as well as DNS server names and IP addresses. Targets are the atomic building block of policies. Targets attributes are described here.
- Target bundles: Bundles are groups of targets defined based on target attributes. For example, a bundle can track all targets tied to the same type of threat. When adding a bundle to your policy, the targets will track changes made by ThreatSTOP. For example, if you add a bundle that tracks Botnet targets and new botnet targets are added to the system, your policy will incorporate the target automatically without requiring you to edit it. Using bundles is the recommended method of blocking threats based on their type or severity to ensure new threats are rapidly added to your policy while avoiding the minutiae of tracking newly published targets.
- User-Defined Lists: User-Defined Lists are lists of IP addresses or domain names. They can be added to your policy to block connections and DNS lookups, or to whitelist them.
Policies are assigned to devices. As their contents are updated throughout the day, firewall and DNS rules are reconfigured to filter the latest IOCs. Policies can also be loaded on SIEM devices using the optional ThreatList feature.
IP and DNS Policies
There are two types of policies, which are assigned to devices based on the device type:
- IP Defense devices use IP Policies, built with IP Targets. They block traffic (inbound and outbound) on firewalls and routers based on source and destination IP addresses.
- DNS Defense devices and Roaming Defense devices use DNS Policies that prevent DNS requests for malicious domains. They can use both domain and IP targets.
-
DNS policies can filter both domains and IP addresses (i.e. IP records returned by the DNS lookups) and can use both domain and IP targets. IP policies use IP targets only.
- IP Policies can apply the following actions:
- Block traffic from and to the IP subnets currently present in the Block target.
- Allow (whitelist) traffic from and to the IP subnets configured in a set of Allow targets.
- Block or allow traffic from IP User-Defined Lists. The action is a setting of the UDL itself.
- DNS Policies can enforce one of multiple RPZ Behaviors. In addition to blocking or whitelisting the DNS lookups, RPZ behaviors can also override the records in the DNS responses. The RPZ behavior is selected when adding a target, bundle or User-Defined List to the policy.
Predefined and custom policies
Predefined policies are managed by ThreatSTOP, and provide several default options to start enforcing a policy quickly. Predefined policies cannot include user-defined lists and can’tb e edited by customers.
Custom policies are created by customers to be tailored to their environment and can include User-defined lists.
User Interface
List view
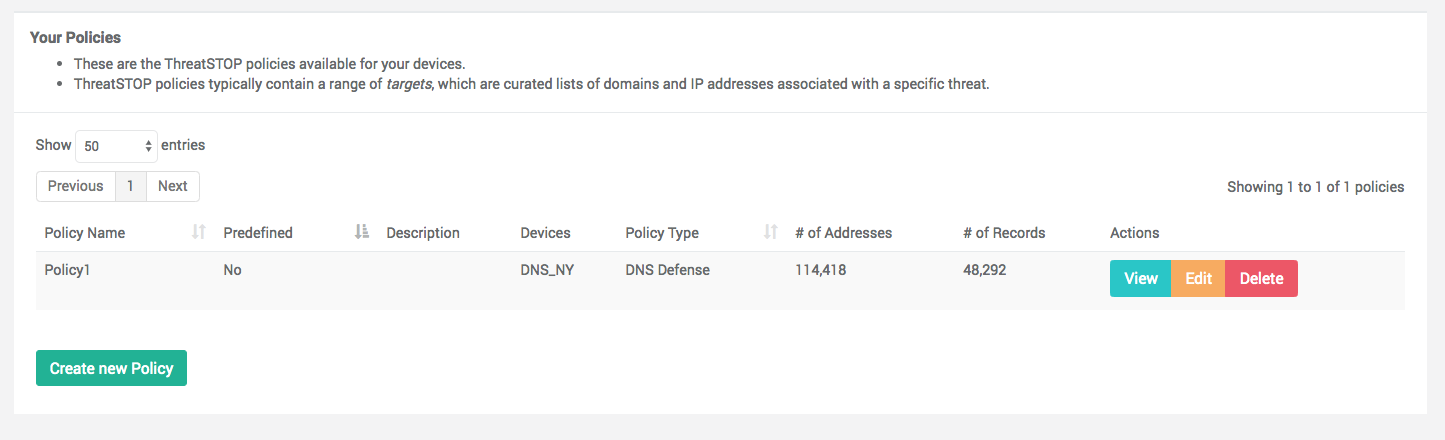
The list of policies available (predefined and custom) in your account is available in the Policies menu. The list displays the following details:
- Policy name, Policy Description and Type.
- Predefined: set to Yes if this policy is a predefined policy managed by ThreatSTOP.
- Number of addresses: for IP Policies, the number of IP addresses covered (block and allow) by the policy; this is different from the number of records because it includes subnets, which can block large group of IP addresses (e.g. Geographical targets).
- Number of records: number of subnets (IP policies) or domains and IP addresses (DNS Policies).
You can edit, view or delete policies from this page. A policy must be inactive (not assigned to a device) before it can be deleted.
Creating a new policy
After clicking the Create new Policy button on the Policy list page, you will be prompted to choose between:
- The type of Policy (IP or DNS) - this can not be changed.
- A blank policy or the policy (custom or predefined) that you want to duplicate as a starting point.
After creating the policy, you can set the following settings:
- Its name (up to 8 alphanumeric characters).
- An optional description.
- For DNS Policies, a default RPZ Action. This will set the default in the GUI when adding bundles and targets. This setting doesn’t control the action of the policy, which is set on a per-target basis.
To configure the policy contents, follow the instruction in the Editing section below.
Once the policy has been created, you can assign it to one or multiple devices or generate ThreatList files for your SIEM device.
Editing policy contents
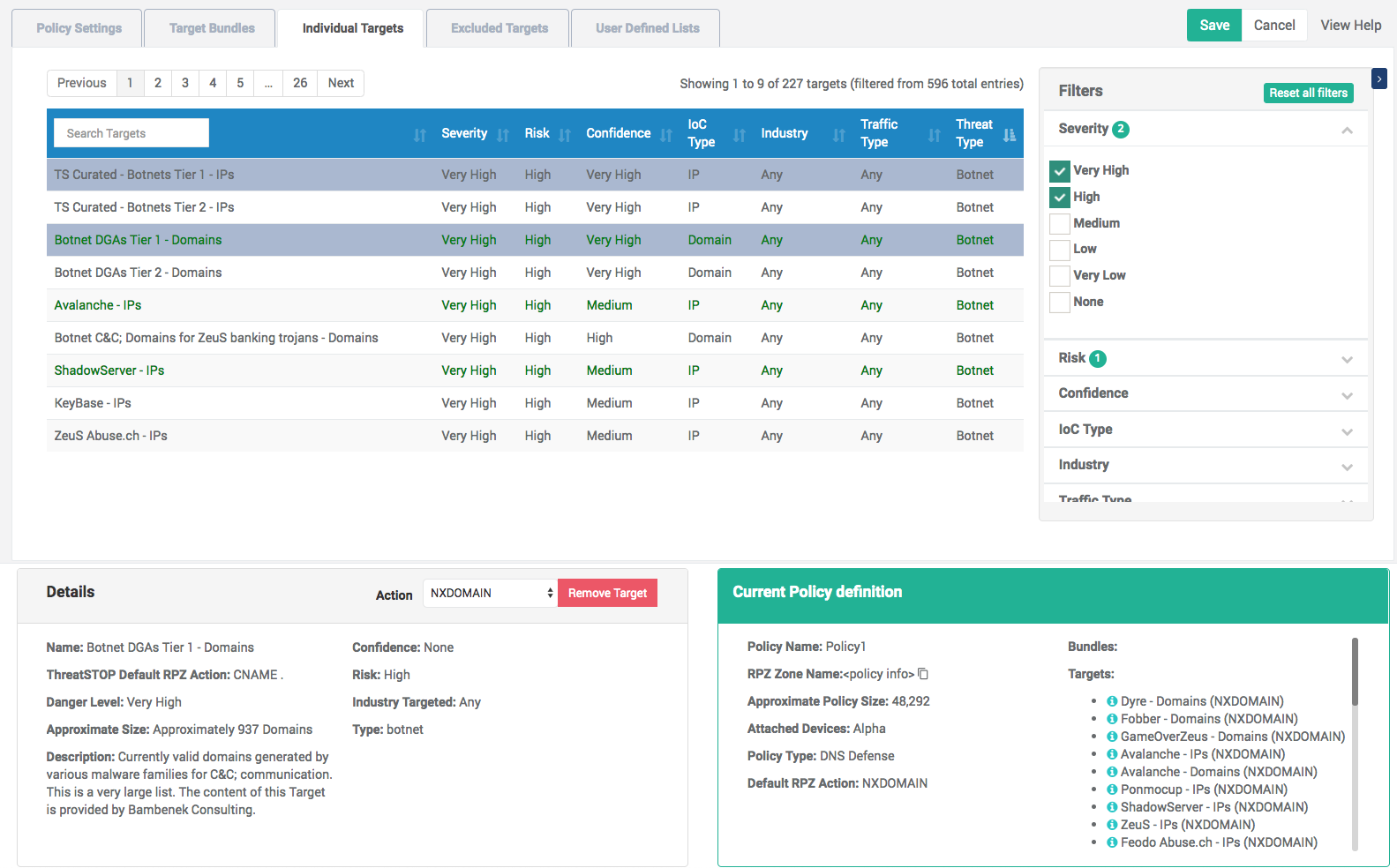
The policy editor is composed of 4 sections.
Tabs
The tabs switch the editor between settings and the type of objects:
- The Settings tab is used to rename the policy or change its description. Important: Web-Automatation devices will reflect a change of policy name automatically within 5 minutes. CLI devices require changing the policy name on devices that use it so they continue retrieving it.
- Target Bundles: select the bundles to add to (or remove from your policy)
- Using bundles is the recommended method of blocking threats based on target attributes without dealing with the minutiae of tracking new targets.
- When you select and add a bundle, your policy will track changes to the bundle made by ThreatSTOP (such as adding or retiring a target that match the bundle configuration).
- You can also add a bundle ‘as targets’, which will add the current targets that make up the bundle, but will not track future changes.
- Targets: add or remove individual targets.
- Marketplace: selection of targets provided by our partners.
- Excluded targets: ensure a target will never be added to your policy, even if included (now or later) in a bundle present in your policy. For example, you might want to include the ITAR bundle but not never block the subnets associated with one of the countries in the bundle.
- User-Defined Lists: UDLs in your account or shared with your account by another user.
List of objects
A list of policy objects, their attributes and filters are displayed below the tabs.
- The list is paginated.
- The list can be sorted by clicking on the table header.
- The Search field will perform a text search in the name and description of the objects.
You can also use the filters on the right hand side to find targets and bundles based on:
- their attribute (Severity, Confidence, Risk, IOC type, Threat Type, Traffic type).
- whether they are already added to your policy (In Policy filter).
The filters can be collapsed with the blue arrow and reset at once with the Reset All Filters button.
To view the full details of a target/bundle and add it to your policy, click on it in the list.
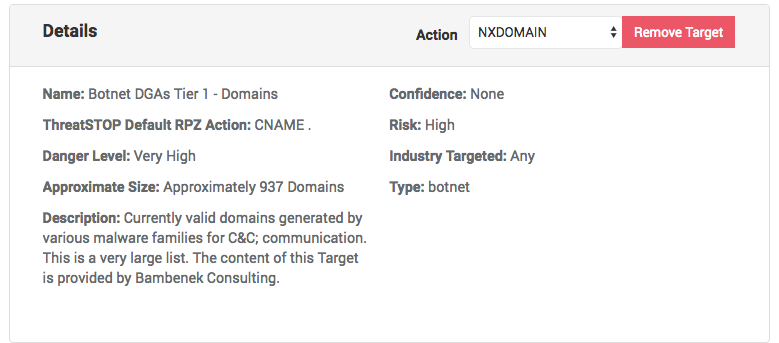
Object details
The details of the currently selected object (Target, bundle or user-defined list based on the active tab) are displayed in the lower left corner.
Bundles
- The name and description of the bundle.
- Its current size (number of records).
- The list of targets currently included by this bundle.
- There are 4 possible actions in the header:
- Adding the bundle: select an action (Block, Allow, or RPZ Behavior) and click Add Bundle. Your policy will track changes made to the bundle.
- Adding the targets currently** present in the bundle. Your policy will *not track changes made to the bundle.
- Change the action (Block > Allow, Allow > Block, or new RPZ Behavior).
- Remove the bundle from the policy.
Marketplace
- The marketplace showcases targets available through our Threat Intelligence Partners.
- These targets may require additional subscriptions. Please contact customer service for access.
Additional targets
- The name and description of the target
- Its current size (number of records). For an IP device, this is approximately to the number of firewall rules. Also note that the size of a target will change over time based on the number of IPs or domains currently associated with the threats.
- The type of Threat tracked by the target (see Target Attributes).
- Danger, Risk and Confidence levels (see Target Attributes).
- There are 3 possible actions on targets:
- Add the target: select an action and click Add Target. Note: most targets can only be added as a block list, not an allow list.
- Change the action from block to allow, or vice-versa, when the target supports both actions.
- Remove the target from the policy.
Excluded targets
- This displays the the same settings as for Individual Targets.
- There are two possible actions:
- Excluding the target, which will remove it from your policy if added using a bundle or as an additional target.
- Clearing the target, which removes it from the exclusion list.
User-Defined Lists
- The name and description of the User-Defined List.
- The number of records (subnets) and addresses (subnets are expanded to count the number of IP addresses).
- A link to the details page for the User-Defined List.
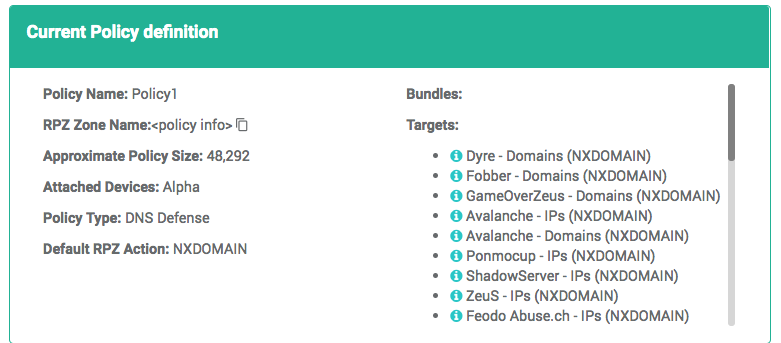
Current Policy Contents
The contents of the policy are displayed in the bottom right corner. They are:
- The name of the policy.
- The bundles, targets, excluded targets and UDLs in the policy.
- The list of devices currently assigned this policy, if any.
- The DNS Zone names associated with the policy. The ThreatSTOP subsystem distributes policies using the DNS protocol. These names are used to configure the policy on CLI devices. There are two zone names for IP devices and one for DNS devices.
Clicking on the information icon next to an object will display its details in the Details section.